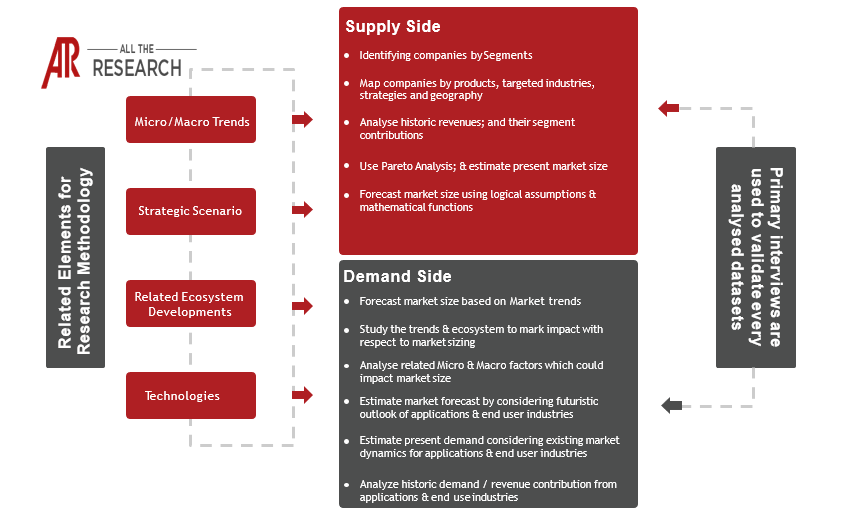
The Internet of Things (IoT) security market is experiencing explosive growth, fueled by the proliferation of connected devices across various industries and the escalating threat landscape targeting these vulnerable endpoints. This segment focuses on safeguarding the confidentiality, integrity, and availability of data and systems within the IoT ecosystem. The market encompasses a wide range of solutions and services designed to protect devices, networks, and cloud infrastructure from cyber threats, data breaches, and operational disruptions. Driven by increasing digitalization and the growing complexity of IoT deployments, the IoT security market is poised for significant expansion in the coming years.
Key Definitions:
Market Drivers:
The IoT security market is primarily propelled by the following factors:
Key Challenges:
Despite its promising growth trajectory, the IoT security market faces significant challenges:
Regulatory Focus:
Governments and industry organizations are actively developing regulations and guidelines to enhance IoT security. Key areas of regulatory focus include:
Major Players:
The IoT security market is highly competitive, with a mix of established security vendors and emerging IoT-focused players. Key players include:
Regional Trends:
The market landscape varies across regions. North America and Europe are currently the leading regions in terms of IoT security spending, driven by high adoption rates of IoT devices, stringent data privacy regulations, and a strong focus on cybersecurity. The Asia-Pacific region is experiencing rapid growth, fueled by the increasing use of IoT in manufacturing, smart cities, and other sectors.
M&A, Fund Raising & Other Trends:
The IoT security market is witnessing a surge in M&A activity, as established security vendors acquire specialized IoT security companies to expand their offerings and gain expertise in this rapidly growing market. Fund-raising activities are also robust, with investors pouring capital into IoT security startups to capitalize on the market's growth potential. Further trends include the adoption of AI and Machine Learning for threat detection, focus on secure-by-design practices, the growth of zero trust architectures, and increasing focus on securing the edge.
CAGR:
The IoT Security market is expected to register a robust CAGR during the forecast period, driven by the factors described above. This growth rate reflects the high demand and potential for solutions in the quickly evolving IoT landscape. (Specific CAGR and forecast period should be included here, taken from the market research report)
The Report Segments the market to include:
By Component:
By Security Type:
By Deployment Mode:
By Organization Size:
By Industry Vertical:

Ask for free product review call with the author

Share your specific research requirements for a customized report
Request for due diligence and consumer centric studies

Request for study updates, segment specific and country level reports
By Component:
By Security Type:
By Deployment Mode:
By Organization Size:
By Industry Vertical:
RSA Conference (San Francisco, CA, USA) - April/May 2024: A large cybersecurity conference with significant IoT security content, including keynotes, sessions, and vendor exhibits.
IoT Security Foundation (IoTSF) Events (Various Locations & Online) - Ongoing: IoTSF hosts webinars, workshops, and training sessions throughout the year focused on secure IoT development, deployment, and operation.
Black Hat USA (Las Vegas, NV, USA) - August 2024: A leading cybersecurity conference with a focus on offensive security, including IoT-related vulnerabilities and exploitation techniques.
DEF CON (Las Vegas, NV, USA) - August 2024: A hacker convention with significant focus on security aspects. Specific topics covered are IoT exploitation, reverse engineering, and embedded systems security.
Infosecurity Europe (London, UK) - June 2024: A major European cybersecurity event featuring sessions and exhibitors relevant to IoT security challenges.
IoT World (Santa Clara, CA, USA) - May 2024: Focuses on the broader IoT landscape, including security solutions, connectivity, and application development.
Embedded World (Nuremberg, Germany) - April 2024: Covers embedded systems and security aspects, often including specific IoT security solutions.
SIA GovSec (Washington D.C., USA) - May 2024: Focuses on security in Government and relevant for connected technologies and IoT.