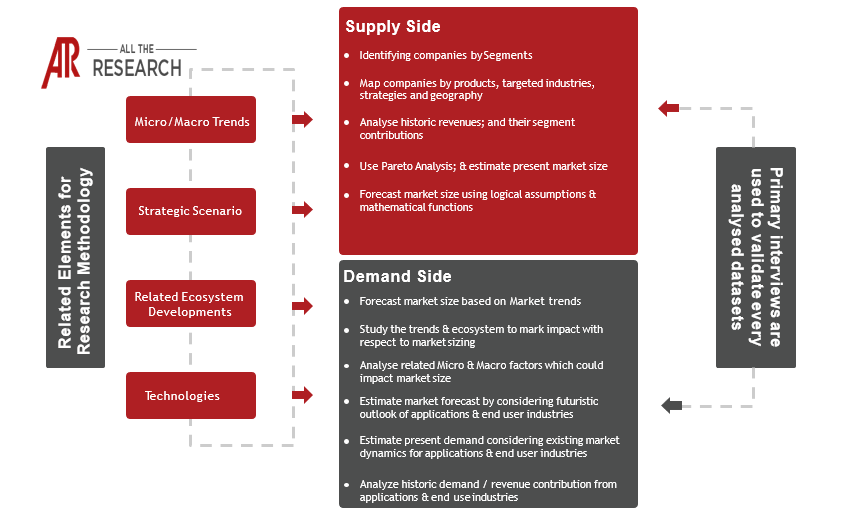
The 5G Security Market is experiencing explosive growth, fueled by the global rollout of 5G networks and the increasing reliance on connected devices. This market focuses on providing robust security solutions that protect 5G infrastructure, connected devices, and the vast amount of data transmitted through these networks. The market encompasses a wide range of technologies, services, and solutions designed to mitigate the unique security challenges posed by 5G's enhanced capabilities, complex architecture, and expanded attack surface.
Market Drivers:
The primary driver of the 5G Security Market is the sheer scale of 5G deployment. The rapid expansion of 5G networks across various industries – from telecommunications and manufacturing to healthcare and automotive – necessitates robust security measures. This is compounded by the increasing number of connected devices (IoT) leveraging 5G's low latency and high bandwidth, exponentially expanding the attack surface for cyber threats.
Key drivers include:
Key Challenges:
Despite the significant growth potential, the 5G Security Market faces several challenges:
Key Definitions:
Within the 5G Security Market, several key definitions are crucial:
Regulatory Focus:
Governments and regulatory bodies are increasingly focused on 5G security, implementing regulations and standards to ensure the secure deployment and operation of 5G networks. Key regulatory initiatives include:
Major Players:
The 5G Security Market is populated by a diverse range of players, including:
Regional Trends:
The 5G Security Market is experiencing growth in all regions, but certain regions are leading the way:
Trends within M&A, Fund Raising, etc.:
The 5G Security Market is witnessing significant activity in M&A and fundraising:
CAGR%
Multiple research reports are projecting the 5G Security market to grow at a CAGR of between 25-35% over the next 5-7 years.
In conclusion, the 5G Security Market is poised for substantial growth in the coming years, driven by the global rollout of 5G networks and the increasing demand for secure connectivity. Overcoming the key challenges related to complexity, skills gap, and evolving threats will be crucial for realizing the full potential of this market and ensuring a secure future for the connected world.
The Report Segments the market to include:
1. By Component
Solutions
Services
2. By Deployment Mode
3. By Enterprise Size
4. By Vertical
5. By Region

Ask for free product review call with the author

Share your specific research requirements for a customized report
Request for due diligence and consumer centric studies

Request for study updates, segment specific and country level reports
1. By Component
Solutions
Services
2. By Deployment Mode
3. By Enterprise Size
4. By Vertical
5. By Region
RSA Conference: Annually, usually in April/May in San Francisco, USA. Covers a broad range of security topics, including 5G security concerns.
Mobile World Congress (MWC): Annually, usually in February/March in Barcelona, Spain. A major telecom event featuring 5G technology advancements and related security discussions.
Black Hat: Annually, usually in August in Las Vegas, USA, and also in other regions at different times. Offers security research, training, and briefings that often cover 5G vulnerabilities and exploits.
DEF CON: Annually, usually in August in Las Vegas, USA. Similar to Black Hat, with a focus on hacking and security research; often features talks on 5G security weaknesses.
5G World: Annually, locations vary. Dedicated to 5G advancements, including discussions on security aspects and challenges.
IEEE International Conference on Communications (ICC): Annually, locations vary. Academic and industry conference covering various communication technologies, including research on 5G security.
IEEE Conference on Network Function Virtualization and Software Defined Networks (NFV-SDN): Annually, locations vary. Explores virtualization and software-defined networking aspects which are critical to 5G security.
SANS Institute Security Conferences: Various locations and dates throughout the year. SANS offers targeted security training and events that may include modules on 5G security.
Cybertech Global Tel Aviv: Annually, usually in January in Tel Aviv, Israel. A major cybersecurity event that often includes sessions on 5G security considerations.
Gartner Security & Risk Management Summit: Annually, various locations. Focuses on enterprise security strategies, including the implications of 5G on risk management.
Layer123 World Congress: Annually, locations vary. Focuses on telecom innovation including security for 5G and related networks.
Online Webinars and Virtual Events: Continuously offered by vendors like Ericsson, Nokia, Samsung, Huawei, and cybersecurity firms specializing in 5G security. Check their websites for schedules.