This report provides a comprehensive analysis of the rapidly evolving Internet of Things (IoT) cybersecurity market, offering invaluable insights into its current state, future prospects, and critical factors shaping its growth trajectory. With the proliferation of connected devices across various industries, the need for robust security measures has become paramount, driving significant market expansion. This in-depth study equips stakeholders with the knowledge and strategic guidance necessary to navigate this dynamic and crucial segment.
Market Overview and Growth Projections:
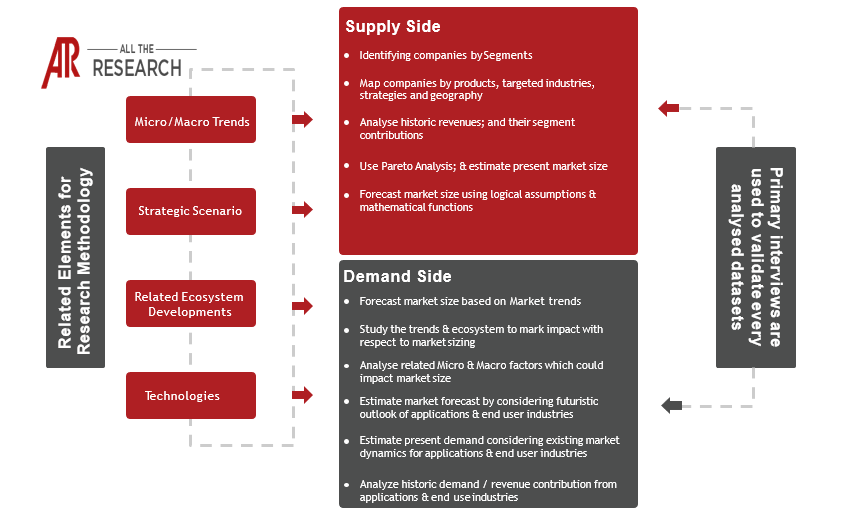
The global IoT cybersecurity market is experiencing substantial growth, projected to reach a significant valuation in the coming years. Driven by escalating cyber threats, stringent regulatory mandates, and increasing adoption of IoT technologies across diverse sectors, the market is poised for significant expansion. Our research indicates a robust Compound Annual Growth Rate (CAGR) over the forecast period, reflecting the ongoing need for sophisticated security solutions. This report provides detailed projections for market size, segmented by various parameters, including device type, security solution, industry vertical, and geographic region.
Key Market Drivers and Restraints:
Several key factors are fueling the growth of the IoT cybersecurity market. These include:
However, the market also faces several challenges that could hinder its growth:
Key Definitions and Segmentation:
This report provides clear definitions of key terms and concepts related to IoT cybersecurity, including:
Regulatory Focus and Industry Landscape:
The report analyzes the impact of various regulatory frameworks and standards on the IoT cybersecurity market. This includes an examination of key regulations such as the GDPR, CCPA, and NIST standards, and their influence on market dynamics. We also delve into the competitive landscape, profiling the major players in the market, including established security vendors, specialized IoT security providers, and emerging start-ups. The analysis includes market share assessments, product offerings, strategic alliances, and competitive advantages of key market participants.
Regional Trends and Market Dynamics:
The report provides a regional analysis, examining the trends and opportunities in key geographic markets, including North America, Europe, Asia-Pacific, and the rest of the world. This includes a discussion of factors such as regulatory environments, adoption rates, and local market dynamics.
M&A, Funding, and Future Outlook:
We provide insights into the M&A activity and funding landscape within the IoT cybersecurity market. This includes analyzing recent acquisitions, investments, and partnerships, providing a glimpse into the strategic priorities of market players and the future direction of the industry. The report concludes with a comprehensive outlook on the future of the IoT cybersecurity market, including key trends, opportunities, and potential challenges. It offers actionable recommendations for stakeholders looking to navigate and succeed in this rapidly growing market. This report will assist you in understanding the overall market, new opportunities, and competitive landscape for the IoT Cybersecurity industry.
The Report Segments the market to include:
By Component:
By Solution:
By Application:
By Deployment Model:
By Organization Size:
By Vertical:
By Region:

Ask for free product review call with the author

Share your specific research requirements for a customized report
Request for due diligence and consumer centric studies

Request for study updates, segment specific and country level reports
Positive Trends:
Adverse Trends:
By Component:
By Solution:
By Application:
By Deployment Model:
By Organization Size:
By Vertical:
By Region:
RSA Conference (San Francisco, CA, and Virtual): A major cybersecurity conference covering all aspects of the field, including IoT security, with keynotes, sessions, and exhibits. (Multiple Dates)
Black Hat USA (Las Vegas, NV, and Virtual): Highly technical conference featuring security research, training, and briefings. Relevant for in-depth IoT vulnerability and threat analysis. (August)
DEF CON (Las Vegas, NV): A hacker convention with workshops, contests, and talks focused on various security topics, including IoT device exploitation and defense. (August)
IoT World (Santa Clara, CA): A leading IoT-focused event with dedicated tracks on security, covering device, network, and data security solutions. (May)
Infosecurity Europe (London, UK): A prominent cybersecurity conference with a significant presence of IoT security vendors and discussions on the latest threats and trends. (June)
ICS CyberSecurity Conference (Various Locations and Virtual): Focuses specifically on the cybersecurity of industrial control systems (ICS) and operational technology (OT) environments, a critical area of IoT security. (Multiple Dates)
Cloud Security Alliance Congress (Various Locations and Virtual): Explores cloud security trends, best practices and standards with IoT often being a focus due to cloud integrations. (Multiple Dates)
SANS Institute Conferences/Webinars: SANS regularly hosts cybersecurity training and events, with courses and webinars dedicated to IoT security, penetration testing, and incident response. (Ongoing)
OWASP Global AppSec (Various Locations and Virtual): Focuses on application security, including the security of web-based IoT devices and applications, offering workshops and talks. (Multiple Dates)
IoT Security Foundation (IoTSF) Events and Webinars: IoTSF organizes events, webinars, and publishes guidance documents on IoT security best practices and standards. (Ongoing)