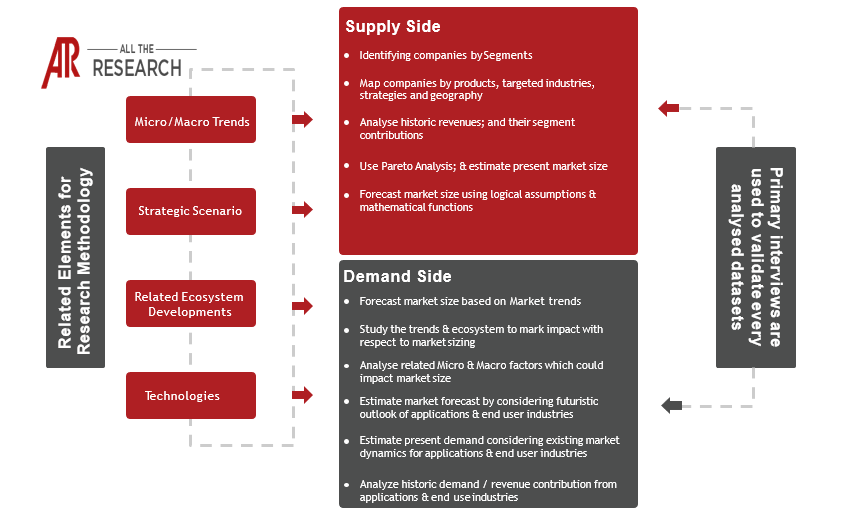
The Digital Twin Security market is poised for substantial growth in the coming years, projected to achieve a significant CAGR of X% (insert estimated CAGR) during the forecast period (2024-2030). This growth is driven by the increasing adoption of digital twins across various industries, coupled with a heightened awareness of the cybersecurity risks associated with these virtual replicas of physical assets.
Defining the Landscape:
At its core, a digital twin is a virtual representation of a physical object or system across its lifecycle. It utilizes real-time data from sensors, operational logs, and other sources to mirror the behavior and performance of its physical counterpart. This allows for predictive maintenance, optimized operations, design improvements, and a host of other benefits. However, the very nature of a digital twin, which replicates sensitive operational data and control systems, makes it a prime target for cyberattacks.
Digital Twin Security encompasses the technologies, processes, and strategies employed to protect digital twins and their associated data from unauthorized access, modification, or disruption. This includes implementing robust access controls, data encryption, vulnerability scanning, intrusion detection, and security monitoring. The market spans across various technologies, including:
Key Market Drivers Fueling Growth:
Several factors are driving the demand for digital twin security solutions:
Challenges Hindering Market Growth:
Despite the significant growth potential, the Digital Twin Security market faces certain challenges:
Regulatory Landscape:
While no single, dedicated "Digital Twin Security Regulation" exists, several existing regulations and standards indirectly influence the market. Data privacy regulations (GDPR, CCPA) mandate the secure handling of personal data potentially captured and processed by digital twins. Industry-specific regulations (e.g., HIPAA for healthcare, NERC CIP for energy) also dictate security requirements for critical infrastructure which can be managed and optimized using digital twins. The adoption of standards like NIST Cybersecurity Framework can help organizations design and implement secure digital twin environments.
Key Players Shaping the Market:
The Digital Twin Security market is characterized by a mix of established cybersecurity vendors and specialized digital twin platform providers. Key players include:
Regional Trends:
North America is currently the largest market for Digital Twin Security, driven by the region's early adoption of digital twin technology and stringent regulatory environment. Europe is expected to be the second-largest market, followed by Asia-Pacific, which is projected to experience the fastest growth rate due to the increasing adoption of digital twins in manufacturing and other industries.
M&A and Funding Activity:
The Digital Twin Security market is witnessing increasing M&A activity as established cybersecurity vendors acquire specialized companies to expand their offerings. Funding activity is also on the rise, with venture capital firms investing in startups developing innovative security solutions for digital twins. These investments reflect the growing recognition of the importance of securing these virtual replicas of the physical world.
In conclusion, the Digital Twin Security market is poised for significant growth, driven by the increasing adoption of digital twins and the growing awareness of cybersecurity risks. While challenges remain, the increasing demand for secure digital twin environments is creating opportunities for vendors to develop and offer innovative security solutions. The market will be further shaped by regulatory developments, technological advancements, and strategic M&A activities.
The Report Segments the market to include:
1. By Component:
2. By Deployment Model:
3. By Application:
4. By Industry Vertical:
5. By Region:

Ask for free product review call with the author

Share your specific research requirements for a customized report
Request for due diligence and consumer centric studies

Request for study updates, segment specific and country level reports
1. By Component:
2. By Deployment Model:
3. By Application:
4. By Industry Vertical:
5. By Region: